
From 1998 to 2000 I was working part-time in the Cognitive Science Lab at the University of Waterloo. I spent most of my time developing a computer model of mental imagery called DIVA (Dynamic Imagery for Visual Analogy). The diva code base has been rewritten into two new packages: cline and symblnet (described below). The diva documentation (and the old code) is here: diva
Developing robust and usable GUIs is labor intensive and in many ways more limiting than the old-school command-line approach. In some form or another, most of my Java projects include a command-line to interact with the user. This command-line has evolved into the cline package - documentation and source code are available: cline.
The symblnet project originated from the associative network I wrote for the DIVA mental imagery model. Symblnet tries to incorporate non-text symbols into the network to produce a richer set of associations (the more associations we can include, the more meaningful our conceptual representations). Another significant difference from the associative network used in DIVA is that symblnet avoids the "isa", "hasa", "likes-to"... relationships that are so prevalent in psychology textbook examples. Relationships are defined based upon pathways between symbols in the network. More information about symblnet and an example applet is available: symblnet.
This is an assignment I prepared when teaching at the Ecole Supérieur d’Informatique in Burkina Faso. It is a relatively straight-forward neural networks exercise that can be distributed amongst a class of students. The basic idea of the assignment is as follows:
One of the CS professors (Oscar) believes he has seen a group of lights in the night-sky that resembles a Roman letter. For example (maybe a little unrealistic):

Oscar is too busy preparing lectures to watch the night-sky, so he uses a video camera to record images from the suspect region. The problem becomes: who has time to sit and watch this long video?
Each student is required to train a neural network that recognizes a specific Roman letter (eg. the letter A), and then write a program that scans through all the frames in Oscar's night-sky video (ten's of thousands - too many to go through by hand). If any letters are recognized, the sequence at which they occur is recorded, and then students can put together their results to establish if, as Oscar suspects, there is a message from space.
Here is the index to the neural networks section of the course, and the actual assignment I gave to the students. The archive of the entire assignment, including the neural networks Java API I prepared for the students and the code to generate videos with embedded messages can be download here. Unfortunately, everything is only available in my grammatically-poor French. Here is a picture of Oscar and I with the class.
The Java Interface Mechanism enables an existing C++ code base to be accessed remotely using a generated Java programming interface. This relies upon two key Java technologies - the Java Native Interface (to call C++ methods from Java), and Remote Method Invocation (to call methods on a Java object that resides on a different machine). The basic process is illustrated below:
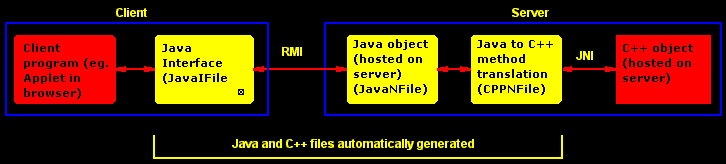
The process is tribute to the idea that anything can be accomplished with enough levels of abstraction. When the idea was initially developed, the intermediate Java classes (3) and the the Java to C++ translation class were manually coded to test the idea. However, when it came time to "JIM-enable" an entire C++ code base for performing financial market risk simulations, a Java program was written to parse C++ header files and automatically generate the intermediate files. Finally, a Java server was developed to host the underlying C++ libraries and accept method calls from remote clients (eg. applets running in web browsers).
The process of making a remote method call and translating a method's parameters to C++ data types has considerable overhead associated with it. As a result, the Java Interface Mechanism is best used with computationally-intense C++ libraries where the overhead associated with making a method call is negligible compared to the time it takes for the C++ method to return. For example, a delay of a few hundred milliseconds to remotely call a C++ method is negligible if the method takes 30 seconds or more to evaluate the worth of a portfolio and return the result.
JIM was successfully used to create a market risk scripting package used by major banking institutions. The technology is owned by TrueRisk (which has since been bought by SunGard Trading and Risk Systems).